サステナビリティSUSTAIN-
ABILITY
ABILITY
Since ANYCOLOR Inc. was founded in May 2017, we have engaged in content business with a focus on VTuber services to fulfill our mission of delivering new magical experiences to all our stakeholders and especially the fans.
We are advancing our day-to-day efforts to keep delivering new magical experiences to people around the world in the aim of becoming a global company that represents Japan, but we can only achieve our goals if we face up to social and environmental issues.
To create a sustainable society, we will continue to strive for sustainable business activities as a platform for helping people the world over to enrich their lives through the content we deliver.
Riku Tazumi, CEO
ANYCOLOR Inc.
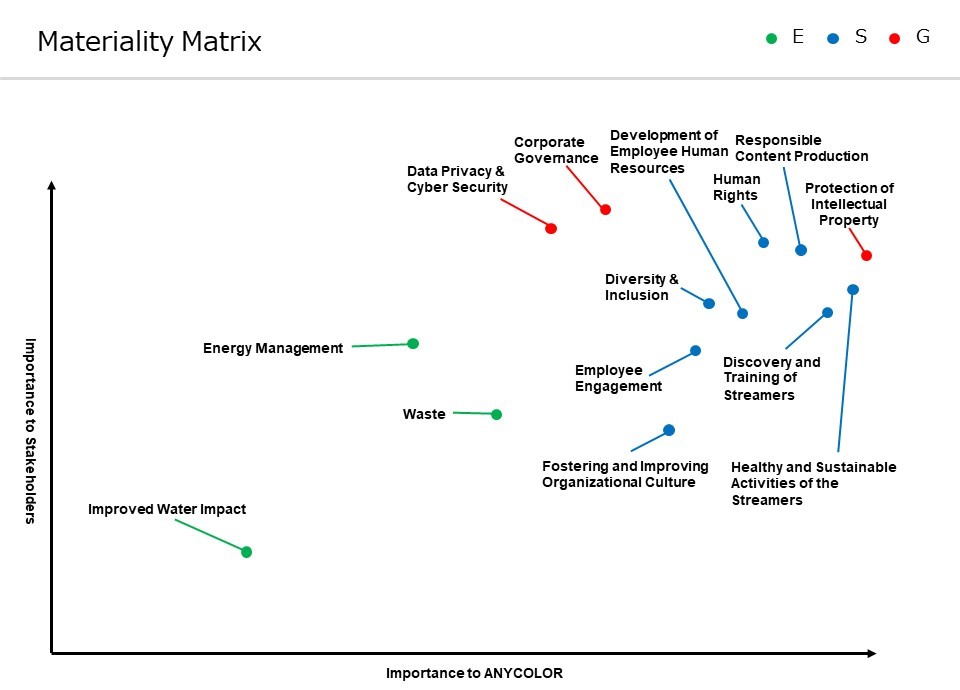
ANYCOLOR has identified 14 ESG issues related to our business and has positioned them on our Materiality Matrix. We selected issues through the following steps.
Step 1: Identification of candidate themes
ANYCOLOR analyzed the expectations and opinions from our valued stakeholders including customers, employees, shareholders, and investors. By reflecting these stakeholders’ expectations, as well as taking into consideration our own internal analysis, GRI standards, SASB and major ESG evaluations, we have selected candidate themes to be focused on.
Step 2: Prioritization
Priority was assigned to the themes identified in Step 1 as ESG issues from the two perspectives of “importance to ANYCOLOR” and “importance to Stakeholders”. As a result, 14 ESG issues were positioned on our Materiality Matrix. A taskforce on prioritization was assembled from the project team, including ANYCOLOR’s CEO.
Step 3. Validation
Our board of directors reviewed and validated the 14 selected ESG issues and the Materiality Matrix.
Click here for details.
The Company respects the human rights of all individuals and recognizes that its mission is to enrich the daily lives of people by continuously offering a new magical experience to the world.
In particular, we believe appropriately taking action against defamation and threatening behavior against Livers affiliated with the Company and protecting their human rights are the bedrock for offering a new magical experience to the world.
In order to respond appropriately to threatening behavior and defamation against Livers affiliated with the Company, we established a special task force to combat threatening behavior and defamation against Livers affiliated with the Company and systematically implement countermeasures against such acts to Livers affiliated with the Company.
Specific activities of the special task force include:
- Quick legal action in cooperation with external lawyers when Livers affiliated with the Company become a target of defamation or threatening behavior
- Provision of a wide variety of support when Livers affiliated with the Company makes a legal demand (Referral to external lawyers, attendance in meetings with external lawyers, evidence gathering, etc.)
- Publication and operation of a Reporting Form to enable reporting on defamation or threatening behavior by those becoming aware of such behavior
- Educational activity to eradicate defamation including activity reports by the special task force
- Actions for Spreading False Information and Defamation to Livers Affiliated with the Company
- Activity Report by a Special Task Force to Combat Threatening Behavior and Defamation (September 2021)
- Actions for Defamation, etc. to Livers Affiliated with the Company
- “Trolling” of the Company and Livers Affiliated with the Company
- Report on Action for Acts in Violation of Privacy Rights to Livers Affiliated with the Company
In addition, the Company established an anti-defamation task force together with the operators of video streaming and posting platforms, creator agencies, and intellectuals in June 2023. The task force will share information among each stakeholder and make suggestions for policies to the government to prevent defamation against all creators.
In order to offer a new magical experience to the world as laid out in the Corporate Mission, the Company is working on the discovery of and support for Livers with outstanding talent. At the same time, the Company considers focusing on the development of Livers for further growth of the Virtual Liver (VTuber) industry and fostering of the VTuber culture as important.
To this end, the Company opened the Virtual Talent Academy in June 2021 as a system to continuously produce Livers who can have long successful careers as Livers.
The Virtual Talent Academy offers technical lessons such as singing, acting, and dancing, fosters the knowledge of streaming technologies and planning ability for live streaming, and provides knowledge cultivated through past business activities of the Company so the students may have long successful careers as Livers affiliated with the Company. The Company regularly provides compliance training to Livers affiliated with the Company after their debut, and in addition to daily support by a talent manager, the Company has a health support system for Livers so that they can continuously engage in the activity with peace of mind. For example, the Company provides them with financial assistance for health checkups and counseling support.
The Company believes thoroughly protecting intellectual property rights of the Company and respecting intellectual property rights of the third parities at the maximum contribute to the sustainable growth of the Company and its business and the rise of culture including the VTuber industry. Therefore, the Company has set forth policies for intellectual properties as below.
Privacy
Basic Policy for Personal Information Protection
As an entertainment company that contributes to society, the Company recognizes the importance of appropriate handling and protection of personal information and has established a personal information protection policy. Our executive officers and employees will work together to comply with this and will do everything possible to protect personal information and the rights and interests of individuals.
Specifically, we collect and use personal information in an appropriate manner according to the Act on the Protection of Personal Information, Japan Industrial Standards (JIS)Personal Information Protection Management System―Requirements, and other relevant laws and regulations.
Management Method of Personal Information
In order to manage personal information appropriately, the Company manages personal information at data centers (collective term for buildings specialized for the installation and operation of Internet servers and equipment for data communication, land, mobile, and IP phones, etc.) in Japan.
Registration in the PrivacyMark System
The Company was granted the right to display “PrivacyMark” by JIPDEC, which means the Company is a business entity with an established system of taking appropriate protection measures for personal information according to the JIS Q 15001:2017 Personal Information Protection Management System.
Security
Formulation of Basic Policies for Information Security
The Company has formulated basic policies for information security measures for the purpose of ensuring the safety of the Company’s internal information assets and contributing to smooth business execution.
Specifically, a manager for control and management of information security was assigned, and under the manager’s instructions, we formulated the basic policy for information handling, established information security regulations, created a system to respond to problems and accidents with information security, and formulated a basic policy for the provision of education on information security measures to each employee.
Network Security Management System
The Company has established a management system and stipulated implementation procedures to appropriately manage the internal network and protect internal information resources from security breaches such as unauthorized access from outside of the Company and virus infections. And under management of the information control manager, the Company engages in design, operation, and management to secure the safety of the internal network.
Management System of Technology Security
Under management of the information control manager, the Company implements the measures listed below for security of the programs to operate internal information by use of all computers, mobile devices including tablet terminals and smartphones, and cellular phones used at the Company (hereinafter, referred to as “Information System”) as well as for the security of the Information System to manage internal information resources and storage media.
- Setting of access authority to internal information resources in consideration of the confidentiality classification of information set forth based on internal standards at the Company and carrying out audits, etc. of access authority setting information
- In regards to access to internal information resources stored in the Information System or storage media, creation of an access authorization system, ensuring the control of access by using individual IDs, passwords, an entry and exit control system, locks, and keys, and implementation of periodic inspections and monitoring to confirm appropriate access control
- Selection of an appropriate contractor to protect the Information System from virus infections, creation of a protection system, and implementation of anti-virus measures for information terminals used by executive officers and employees
- Establishment of an emergency response policy in case of emergencies such as the discovery of unauthorized access to information terminals and occurrence of problems such as virus infections
Physical Security Measures
For the purpose of protecting information terminals and network devices that comprise the information network system primarily from damage or theft and protecting internal information assets of the Company by this means, the Company has built a management system and implements physical security measures for the introduction, installation, and operation method of information devices such as entry and exit management.
Thorough Provision of Security Education
The Company provides e-learning for security on a regular basis to allow all employees including temporary staff members to acquire knowledge for information security at the necessary level for work, to raise the security awareness of employees, and to increase the information security level of the Company as a whole.
Policy for the Handling of Connections with External Networks
In order to prevent leaks of and unauthorized access from outside of the Company to internal information, the Company has stipulated a handling method when connecting the internal network to an external network system comprised of external personal computers, mobile devices, servers, cloud servers, etc. Under management of the information control manager, the network is designed in detail and operated for connecting with external networks according to the following rules.
- Security measures such as the use of firewalls must be implemented. When a standalone computer of the Company is connected to an external network, measures to prevent unauthorized access from the outside by using the standalone computer as a security hole must be implemented.
- Executive officers and employees authorized to access the internal network from outside of the Company must be limited. More advanced identity authentication such as the use of one-time passwords must be used in particular when executive officers and employees connect to the internal network by remote access and when those who are not executive officers or employees of the Company access the Company’s internal network with permission due to participation in a Company project.
- Access authority granted to those who are not executive officers or employees of the Company due to the need to access the internal network of the Company for reasons such as participation in Company projects must be limited to the absolute necessary level for work.
- Response when a problem occurs to the network such as unauthorized access to the network from inside or outside of the Company must be decided.
Comprehending Factors Related to the External Environment
The Company will execute appropriate security and safety protocols when storing personal information in foreign countries, in accordance with the regulations provided by legal administrations of the relevant country, such as the Personal Information Protection Commission in Japan, after having comprehended the system for the protection of personal information in the country where such information is retained.
| Data Item | FY2024 | FY2025 | |||
| Governance | |||||
| No. of whistleblowing cases | 1 | case | 2 | cases | |
| No. of cases where legal action was taken for the Company for corruption or bribery, etc. | 0 | cases | 0 | cases | |
| Employment & Diversity*1 | |||||
| No. of employees | Overall | 430 | employees | 532 | employees |
| Ratio of male and female | Male | 55.3 | % | 52.1 | % |
| Female | 44.7 | % | 47.9 | % | |
| Ratio of female managers | 12.7 | % | 18.6 | % | |
| Average age | 31.2 | years old | 31.8 | years old | |
| Wage difference by gender | 76.1 | % | 78.3 | % | |
| Labor Practices and Welfare | |||||
| Yearly working hours (Average per person) | 2141.8 | hours | 2119.2 | hours | |
| Yearly overtime work hours (Average per person) | 178.5 | hours | 161.3 | hours | |
| Paid holiday use rate | 74.2 | % | 72.1 | % | |
| Childcare leave use rate*2 | No. of employees | 8 | employees | 4 | employees |
| Use rate | 57.1 | % | 50.0 | % | |
| Return to work rate | 100 | % | 100 | % | |
| Health and Safety | |||||
| Number of occupational accidents | 1 | case | 2 | cases | |
| Rate of employees taking the questionnaire to assess their stress level | 86.4 | % | 75.1 | % | |
| Actions for defamation and threatening behavior against Livers affiliated with the Company | |||||
| Number of cases handled, including lawsuits*3 | 124 | cases*4 | 95 | cases*5 | |
- *1 : Same definition used in the Securities Report
- *2 : Number of employees who took child leave divided by the number of employees who added dependents.
- *3 : Refer to the Activity Report on “Anti-Harassment and Defamation Response Team” for details. (Oct. 2025) (Oct. 2024)
- *4 : Reporting period is Nov. 2023 ~ Oct. 2024
- *5 : Reporting period is Nov. 2024 ~ Oct. 2025